Java教程
基于 Traefik 的 ForwardAuth 配置
本文主要是介绍基于 Traefik 的 ForwardAuth 配置,对大家解决编程问题具有一定的参考价值,需要的程序猿们随着小编来一起学习吧!
前言
Traefik 是一个现代的 HTTP 反向代理和负载均衡器,使部署微服务变得容易。
Traefik 可以与现有的多种基础设施组件(Docker、Swarm 模式、Kubernetes、Marathon、Consul、Etcd、Rancher、Amazon ECS…)集成,并自动和动态地配置自己。
系列文章:
- 《Traefik 系列文章》
今天我们基于 Traefik on K8S 来详细说明如何通过 forwardauth 实现认证功能,并通过 ForwardAuth 和 OAuth 2.0 或 CAS 进行集成。
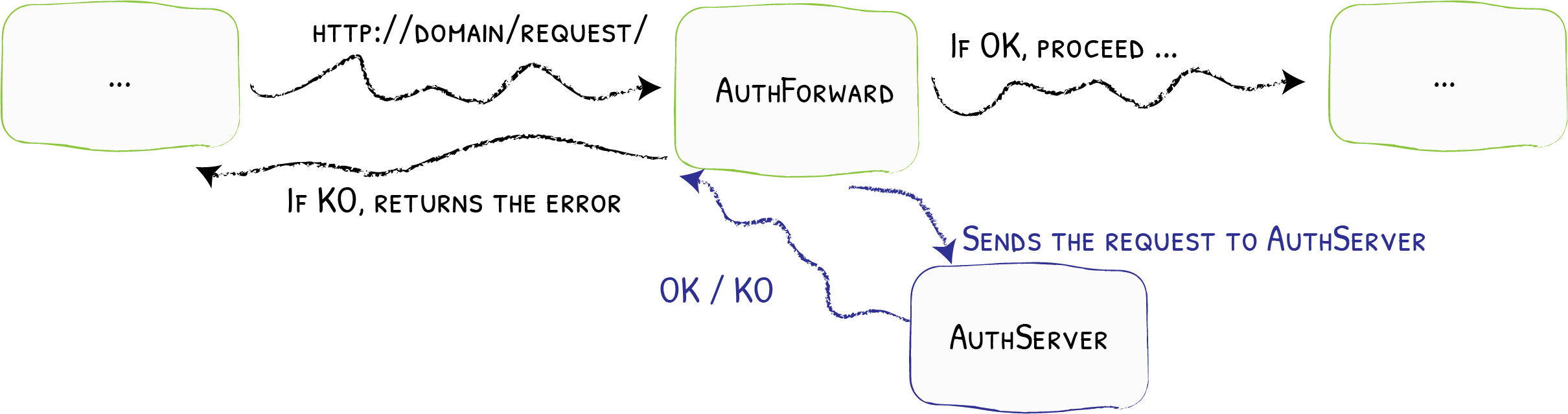
ForwardAuth 中间件将身份验证委托给外部服务。如果服务响应代码为 2XX,则授予访问权限并执行原始请求。否则,将返回身份验证服务器的响应。
ForwardAuth 的简单配置
创建 ForwardAuth 中间件,具体如下:
apiVersion: traefik.containo.us/v1alpha1
kind: Middleware
metadata:
name: forward-auth
spec:
forwardAuth:
# 路径视具体情况而定
address: http://your_auth_server/oauth2.0/validate
authResponseHeaders:
- Authorization
trustForwardHeader: true
另外一般出于安全,会再加一些安全相关的 header, 如下:
apiVersion: traefik.containo.us/v1alpha1
kind: Middleware
metadata:
name: secure-header
spec:
headers:
browserXssFilter: true
contentTypeNosniff: true
customResponseHeaders:
Cache-Control: max-age=31536000
Pragma: no-cache
Set-Cookie: secure
forceSTSHeader: true
stsIncludeSubdomains: true
stsSeconds: 14400
当然,也是出于安全,会用到 HTTP 重定向到 HTTPS.
之后,创建 IngressRoute 的示例配置如下:
apiVersion: traefik.containo.us/v1alpha1
kind: IngressRoute
metadata:
name: alertmanager
spec:
routes:
- kind: Rule
match: Host(`ewhisper.cn`) && PathPrefix(`/alertmanager/`)
middlewares:
- name: redirectshttps
- name: secure-header
- name: forward-auth
services:
- name: alertmanager
port: 9093
🎉完成!
使用 OAuth Proxy 和 Traefik ForwardAuth 集成
创建 ForwardAuth 401 错误的中间件
Traefik v2 ForwardAuth 中间件允许 Traefik 通过 oauth2-agent 的 /oauth2/auth 端点对每个请求进行身份验证,该端点只返回 202 Accepted 响应或401 Unauthorized的响应,而不代理整个请求。
oauth-errors 和 oauth-auth 中间件
---
# 用途:给 oauth url 加 headers
apiVersion: traefik.containo.us/v1alpha1
kind: Middleware
metadata:
name: auth-headers
spec:
headers:
sslRedirect: true
stsSeconds: 315360000
browserXssFilter: true
contentTypeNosniff: true
forceSTSHeader: true
sslHost: ewhisper.cn
stsIncludeSubdomains: true
stsPreload: true
frameDeny: true
---
# 用途:forwardauth
apiVersion: traefik.containo.us/v1alpha1
kind: Middleware
metadata:
name: oauth-auth
spec:
forwardAuth:
address: https://oauth.ewhisper.cn/oauth2/auth
trustForwardHeader: true
---
# 用途:forwardauth 返回 401-403 后重定向到登录页面
apiVersion: traefik.containo.us/v1alpha1
kind: Middleware
metadata:
name: oauth-errors
spec:
errors:
status:
- "401-403"
service: oauth-backend
query: "/oauth2/sign_in"
oauth 的 IngressRoute 配置:
apiVersion: traefik.containo.us/v1alpha1
kind: IngressRoute
metadata:
name: oauth
spec:
routes:
- kind: Rule
match: "Host(`ewhisper.cn`, `oauth.ewhisper.cn`) && PathPrefix(`/oauth2/`)"
middlewares:
- name: auth-headers
services:
- name: oauth-backend
port: 4180
需要用到 oauth 的其他应用的 IngressRoute 配置:
apiVersion: traefik.containo.us/v1alpha1
kind: IngressRoute
metadata:
name: alertmanager
spec:
routes:
- kind: Rule
match: Host(`ewhisper.cn`) && PathPrefix(`/alertmanager/`)
middlewares:
- name: redirectshttps
- name: oauth-errors
- name: oauth-auth
services:
- name: alertmanager
port: 9093
🎉完成!
📚️参考文档
- ForwardAuth | Traefik | v2.0
- Overview | OAuth2 Proxy (oauth2-proxy.github.io)
EOF
三人行, 必有我师; 知识共享, 天下为公. 本文由东风微鸣技术博客 EWhisper.cn 编写.
这篇关于基于 Traefik 的 ForwardAuth 配置的文章就介绍到这儿,希望我们推荐的文章对大家有所帮助,也希望大家多多支持为之网!
您可能喜欢
-
怎么修改Kafka的JVM参数?-icode9专业技术文章分享12-24
-
线下车企门店如何实现线上线下融合?12-23
-
鸿蒙Next ArkTS编程规范总结12-23
-
物流团队冬至高效运转,哪款办公软件可助力风险评估?12-23
-
优化库存,提升效率:医药企业如何借助看板软件实现仓库智能化12-23
-
项目管理零负担!轻量化看板工具如何助力团队协作12-23
-
电商活动复盘,为何是团队成长的核心环节?12-23
-
鸿蒙Next ArkTS高性能编程实战12-23
-
数据驱动:电商复盘从基础到进阶!12-23
-
从数据到客户:跨境电商如何通过销售跟踪工具提升营销精准度?12-23
-
汽车4S店运营效率提升的核心工具12-23
-
ERP 系统开发案例:用 PERT 图打造高效项目管理12-23
-
初创团队必备!全面解析支持甘特图的项目管理工具与功能特点12-23
-
任务进度跟踪不再难!可视化项目协作工具精选12-23
-
看板工具为汽车销售门店协作赋能:关键方法12-23
栏目导航